Data leaks can occur in many ways like hacking, phishing, etc. But have you ever thought about how something as small as a USB drive could put your sensitive information at risk? Imagine, someone plugs in a USB, quickly copies your private files, and walks away without anyone noticing. Scary, right?
That’s where USB blocking comes in! It prevents unknown devices from connecting to your computer and keeps your data secure from any theft or harmful viruses. In this blog, you’ll understand how USB blocking works, why it’s a smart choice to protect your information, and how it can help prevent costly data leaks.
What is USB Blocking?
USB blocking is a security measure that is used to prevent unauthorized access to or usage of a USB port on a device. By stopping external USB devices, such as flash drives, external hard drives, or other gadgets, from connecting, USB blocking helps protect against data stealing, computer viruses, and illegal file sharing. This practice is widely used by many companies to safeguard their sensitive data from data breaches.
There are several methods to implement USB blocking. Software solutions use security programs or tools to stop or control USB access. In big companies, IT teams often set rules to block USB use on many devices at once. Also, physical USB locks can be used to block the ports, stopping people from plugging in unwanted devices.
How do USB Blockers function?
USB blockers function by restricting or disabling access to USB ports on a device, preventing unauthorized devices from connecting. They can work in different ways, depending on the type of blocker used.
- Software USB blockers use security programs or settings to control USB access. They can disable the ports entirely, allow only approved devices, or make the ports read-only, which means data can be read but not copied or changed.
- Software USB blockers use security programs or settings to control USB access. They can disable the ports entirely, allow only approved devices, or make the ports read-only, which means data can be read but not copied or changed.
Overall, USB blockers help to prevent malware, data thefts, and unauthorized file transfers by limiting who can access ports.
Essential Features of Reliable USB Blockers (Infographics )
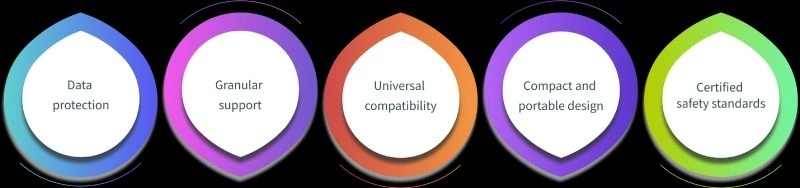
When it comes to USB security, features matter. Don’t settle for less. Here are some of the essential features that you should look for!
Data Protection
This is the basic and common feature that every USB blocker you choose should have. Look for a feature where it must offer strong data protection to prevent unauthorized access, malware, etc. It should protect your sensitive data and stop it from being copied or transferred by blocking the USB ports. The best USB blockers even have some extra quality features such as encryption, read-only modes, or access controls making it harder for hackers or unknown people to misuse your device.
Granular Support
The best USB blockers provide granular support allowing you to customize settings according to your organization’s needs. This lets you control device access by allowing trusted USB drives and blocking unapproved ones. You can even set it to read-only, so files can be viewed but not changed. As an administrator, you can set different rules for groups or individuals in the company based on their jobs and data needs. This adds extra safety by letting only devices connect to important systems.
Universal Compatibility
For maximum effectiveness, the USB blocker you choose should offer universal compatibility with various devices and operating systems. A good USB blocker should work on Windows, macOS, Linux, and mobile devices, giving the same protection on all platforms. You should also look for support for USB 2.0, 3.0, and newer versions to ensure its future proof. This huge compatibility makes it easy for you to use in businesses, schools, or even at home, no matter what hardware you're working with.
Compact and Portable Design
If you’re a traveler, then opt for a compact and portable USB blocker. The one you choose should be easy to carry and ideal. A lightweight blocker is ideal if you travel often or work remotely, it helps you protect your data wherever you are. Look for a device that installs quickly and doesn’t usually require extra software. A portable USB blocker keeps your data safe wherever you go.
Certified Safety Standards
To make sure the USB blocker you choose is safe and reliable, look for the one that follows certified safety standards. Check for products with ISO, FCC, CE, or RoHS certifications as they indicate that they meet international safety and quality rules. Certified blockers are once checked to make sure they work safely and last long, giving you strong protection. Using a trusted blocker helps you stay within the rules and protect both your data and your reputation.
Why is USB Blocking Crucial for Organizations?
USB blocking is crucial for organizations because it protects sensitive data from being stolen or misused. This plays a crucial role for businesses that deal with customer data, money records, or secret information.
It also helps to prevent malware attacks, as USB devices carry some viruses or ransomware that pass through the network and cause some serious damage. Not only this, USB blocking prevents physical attacks such as “USB drop” attacks, where fake USB drives with viruses are planted to trick employees into plugging them, and “juice jacking” where it indicates charging cables steal sensitive data or put in some harmful programs.
USB blocking helps companies follow data protection rules. Many industries have strict privacy laws, like GDPR, HIPAA, or PCI DSS, that say they must keep private information safe. By controlling USB use, companies can follow these rules and avoid heavy fines.
How USB Blocking Prevents Data Leaks
1. Restricts Unauthorized Access
USB blocking stops unknown devices from connecting to company computers. This prevents employees, contractors, or outsiders from copying or stealing private data. Without USB blocking, someone could quickly plug in a flash drive and extract confidential information in seconds. This is particularly important for industries that handle financial records, customer data, or trade secrets. Even a small data leak can definitely result in financial loss or legal consequences. By disabling or restricting the USB ports, companies can protect their data from both insider and external threats.
2. Control File Transfers
Limiting USB access can help organizations control who is allowed to share the files. With USB blocking, only approved devices or users with special permission can use USB ports. This lowers the risk of data leaks because employees cannot just plug in their own USB drives to copy private information.
Additionally, companies can set read-only permissions to some files where it allows only to read not to edit, which eventually strengthens data security. This indicates that even if USB devices are used for business, data theft or modification can be still restricted.
3. Prevents Malware Infections
USB blocking also helps stop malware, which can cause data leaks. Unknown or unapproved USB devices might have harmful software that can steal, damage, or erase important information. For example:
- Spyware: Secretly tracks and collects data
- Key loggers: Captures keystrokes, which allows hackers to steal login credentials
- Ransomware: Encrypts files and demands money to restore access.
Blocking USB access lowers the risk of harmful software getting into company systems. This protects their data and keeps their network safe. It also stops malware from spreading to other parts of the company’s network.
4. Closes Security Gaps
USB blocking fixes a big security weakness that hackers often use. Stopping unknown data transfers helps companies protect their information and reduce data leaks. It helps them to follow privacy rules such as GDPR, HIPAA, and PCI DSS, by keeping data safe.
In addition, USB blocking also reduces insider threats, which are often ignored. Employees or contractors with access to private information might try to steal data using USB drives. By closing this security hole, companies greatly lower the risk of internal data leaks.
Best Practices to Ensure USB Security (Infographics )
Here are some effective practices to strengthen your USB security.
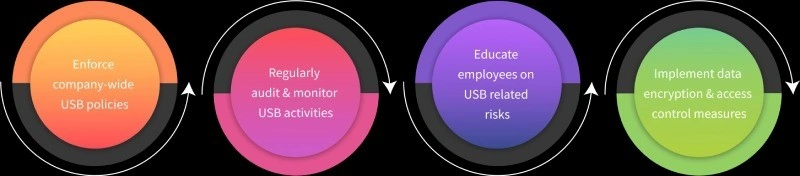
1. Enforce Company-Wide USB Policies
To improve USB security in your company, you should create and follow some USB rules. Define who can access USB ports under what conditions. For example, you can limit USB access to authorized persons only or allow USB ports that meet specific security standards. The rules should also explain what types of files can be moved to or from USBs. You can also set up automatic USB blocking on all devices, so only trusted USBs will work. By standardizing these rules across the organization, your company can reduce the risk of data leaks.
2. Regularly Audit and Monitor USB Activities
To maintain strong USB security, it is important to regularly monitor and audit USB activities. Use USB control software to track and log all USB connections and file transfers. This way, your IT team can easily review those logs to identify any suspicious activity such as unauthorized file transfers or the use of unapproved devices.
Regular audits help you find any security gaps and ensure you’re following your company policies. Keeping track of USB use can make it easier to solve issues later. Real-time monitoring makes your security stronger by warning you about possible unintentional threats so you can act fast.
3. Educate Employees on USB-Related Risks
Employee awareness is essential for USB security. You should often teach employees about the dangers of using USB devices, such as data stealing, viruses, and unauthorized access.
Teach your employees on how to recognize suspicious USB drives and help them understand the risks of using unapproved or unknown devices. Your training should also cover best practices, such as avoiding personal USB drives for work purposes and only using company-authorized devices. This lowers the risk of data leaks and security problems.
4. Implement Data Encryption and Access Control Measures
To make your USB security stronger, you should lock data with encryption and use access controls. Encryption protects your sensitive data, even if the USB is lost or stolen because only people with the right key can open the data.
You can also set up some access controls, like letting only trusted USBs connect, adding more safety. This makes sure that only safe devices can link to your network. Using read-only modes stops people from copying or sending data, protecting your data from being stolen.
How Time Champ Improves USB Blocking to Safeguard Your Data
Time Champ's Data Loss Prevention (DLP) feature includes a great USB blocking tool to protect your sensitive data. It blocks unauthorized USB devices from connecting to your system, preventing potential risks like malware or data theft. This ensures that only trusted devices can access your information, keeping it safe.
Time Champ also provides instant notifications whenever a USB device is plugged in. You can customize alerts to get updates via desktop or email, along with screenshots of user activity. This makes it easy to quickly spot and respond to any unauthorized USB connections, helping you protect your data with ease.
Stay compliant and secure with Time Champ’s USB blocking solution.
Monitor, control, and protect your data with confidence.
Signup for FreeBook DemoFinal Thoughts
In conclusion, USB blocking is an effective security measure to protect your data from loss of data, viruses, and unauthorized copying. Through the regulation of USB access, you can protect your data from leakage, keep away from malware, and adhere to the rules on privacy. When you combine USB blockers with clear policies, employee training, and monitoring, your overall data security improves quickly. With the right tools in place, you can keep your data safe and avoid consequences.
Frequently Asked Questions
Look for a USB blocker that is easy to setup, and which has strong security features such as encryption, compatibility with multiple devices and operating systems. It should let you customize access permissions for different users.
Absolutely! USB blocking helps businesses follow security regulations such as GDPR, HIPAA, and PCI DSS by making sure that sensitive data is protected from unauthorized access and transfer.
USB blocking helps prevent malware from entering the company network via USB devices. When USB ports are blocked, it is harder for viruses or harmful files from infected devices to spread. This helps keep the network safe.
No, setting up a USB blocker is typically quick and easy. Most software blockers offer simple installation and configuration, while physical blockers can be plugged in or attached to USB ports without any technical skills.
