Discover the emerging corporate trend of coffee badging and how it’s transforming workplace dynamics.
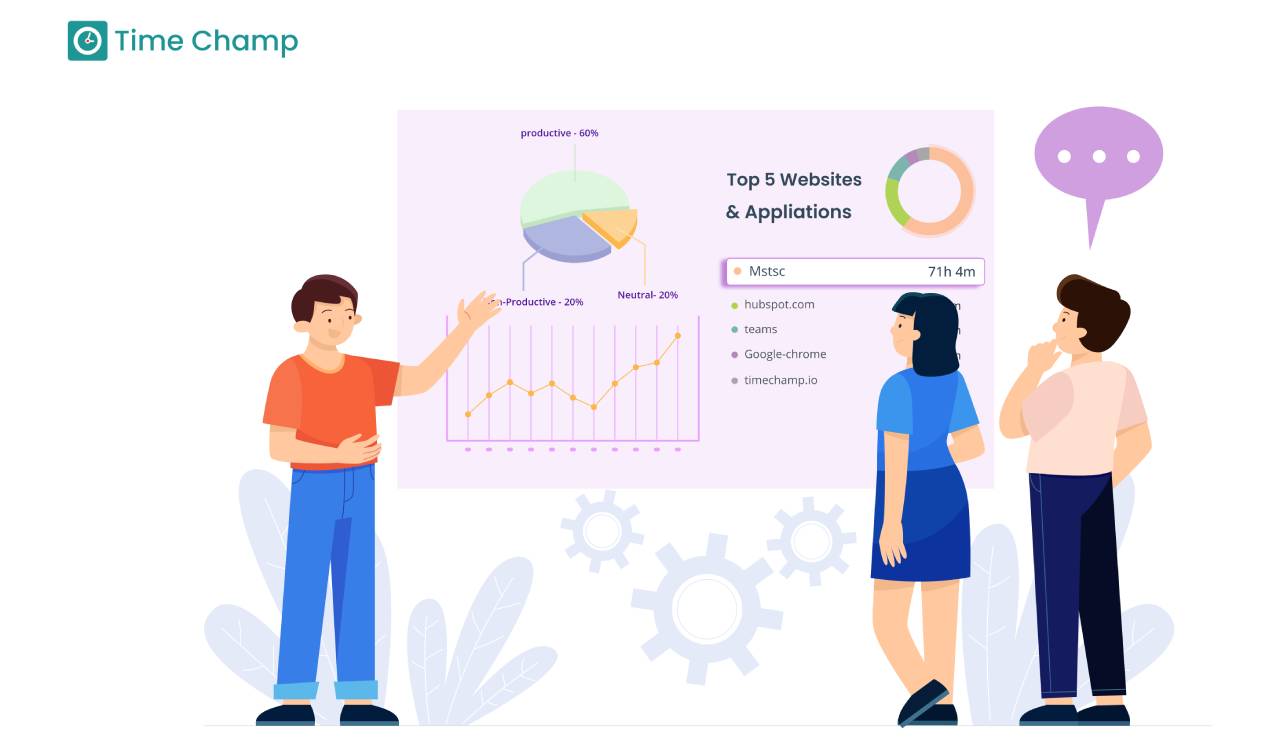
Employee Activity Reports: How To Write and Analyze
Discover how to write and interpret employee activity reports to gain insight and drive better business results.





Recent Comments
No comment found.