Are you sure your business files are safe? Cyber threats are increasing and file integrity monitoring tools are now essential for businesses. A single unauthorized file change can lead to data breaches, compliance issues, or even financial loss.
Even small, unnoticed changes in critical files can open the door to security risks. Whether it's a cyberattack, system error, or accidental modification, not knowing what’s happening with your files can put your business at risk.
Don’t worry! File integrity monitoring tools help you to protect your business by detecting and alerting you if any unauthorized file access happens without having permission. In this blog, you will explore the best FIM tools to help you secure your business files. Let’s dive in!
What is File Integrity Monitoring Tool?
A file integrity monitoring (FIM) tool is a security solution that tracks changes to important files and system data. FIM tools can detect if a file is modified by a hacker, system error or mistakenly. These tools compare the current version of a file with a trusted original version. If there is a difference, you get an alert. This helps businesses protect sensitive data, prevent security threats, and meet compliance requirements.
Top File Integrity Monitoring Tools
Choosing the right file integrity monitoring tool is important for keeping your business data secure. These tools help you track file changes and detect unauthorized access. Let’s take a look at some of the best file integrity monitoring tools that can help protect your business
1. Solarwinds Security Event Manager
SolarWinds Security Event Manager (SEM) is a comprehensive security information and event management (SIEM) solution that includes robust file integrity monitoring capabilities. It helps organizations detect and respond to unauthorized changes to critical files, folders, and registry settings, enhancing overall data security.
Key Features
- Real-Time File Monitoring: SEM continuously monitors sensitive files and directories, alerting you immediately to any unauthorized modifications.
- Detailed Audit Trails: The tool provides comprehensive logs of file changes, including information on who made the change and when, aiding in forensic analysis.
- Compliance Reporting: SEM offers pre-built reports to help meet various compliance requirements by demonstrating effective file integrity monitoring practices.
- Integration with SIEM: As part of a broader SIEM solution, SEM correlates file integrity events with other security data to provide a holistic view of potential threats.
Best for
SolarWinds Security Event Manager is best for businesses and IT teams that need a powerful SIEM solution with built-in file integrity monitoring.
2. Time Champ
Time Champ is a powerful workforce management and productivity tracking software that also includes Data Loss Protection (DLP) features. One of its key security capabilities is file monitoring, which helps businesses track and protect critical files from unauthorized modifications, deletions, or transfers. This feature ensures that sensitive business data remains secure and compliant with industry regulations.
Key Features
1. File Monitoring Configuration
Administrators can configure file monitoring settings to manage and track file activities effectively.
- Real-Time File Monitoring: SEM continuously monitors sensitive files and directories, alerting you immediately to any unauthorized modifications.
- Enter Folder Paths to Monitor: Specify directories to track file activities.
- Monitor up to 1000 changes: This ensures real-time tracking of file modifications.
- Selected File/Folder Paths: Displays the list of currently monitored files and directories.
This configuration allows businesses to set up proactive monitoring and identify unauthorized file access or suspicious activity.
2. File Monitoring Logs
The File Monitoring Logs feature displays detailed records of file modifications, including:
- User Name: Identifies the employee responsible for file changes.
- Folder Paths: Shows the location of the file that was modified.
- Action Made: Indicates the type of action taken (e.g., Edited, Renamed, Deleted, Location Changed).
- Last Modified: Provides a timestamp for when the action occurred.
This feature allows businesses to track unauthorized file changes and take action against potential data breaches or policy violations.
Best for
Time Champ is best for businesses looking for a complete workforce management and security solution that includes file integrity monitoring, data loss prevention , and employee productivity tracking.
3. Tripwire File Integrity Manager
Tripwire File Integrity Manager is a specialized solution focused on detecting and reporting unauthorized changes to files and system configurations. It provides organizations with the necessary tools to maintain system integrity and comply with regulatory standards.
Key Features
- Automated Change Detection: The tool automatically identifies and alerts you to unauthorized or unexpected changes to critical files and configurations.
- ChangeIQ Technology: Differentiates between routine, authorized changes and those that may pose security risks, reducing false positives and focusing attention on critical issues.
- Scalability: Designed to handle large and complex IT environments, making it suitable for enterprises with extensive networks.
Best for
Suited for enterprises needing high-level security and compliance support, with automated file integrity monitoring and advanced threat detection.
4. ManageEngine Event Log Analyzer
ManageEngine Event Log Analyzer is a comprehensive log management and analysis tool that includes robust file integrity monitoring (FIM) capabilities. It helps organizations monitor and protect sensitive data by detecting unauthorized changes to critical files and folders in real-time.
Key Features
- File Monitoring: Continuously tracks changes such as additions, deletions, and modifications to files and directories across Windows and Linux systems.
- Instant Alerts: Sends immediate notifications upon detecting unauthorized file activities, enabling swift response to potential security incidents.
- User Behavior Analytics: Utilizes user behavior analytics to detect anomalies in file access patterns, helping identify potential insider threats.
Best for
A great choice for IT administrators who need a centralized platform for monitoring file changes, analyzing security logs, and ensuring compliance.
5. OSSEC
OSSEC is an open-source Host-based Intrusion Detection System (HIDS) that provides powerful file integrity monitoring (FIM) capabilities. It is designed to detect unauthorized modifications to files, aiding in the prevention of data breaches and ensuring system integrity.
Key Features
- Comprehensive File Monitoring: Combines file integrity monitoring with log analysis to provide a holistic view of system activities and potential security threats.
- Log Analysis Integration: Sends immediate notifications upon detecting unauthorized file activities, enabling swift response to potential security incidents.
- Rootkit Detection: Includes capabilities to detect and alert on rootkit installations, enhancing the overall security of the monitored systems.
- Cross-Platform Support: Supports multiple operating systems, making it a versatile choice for diverse IT environments.
Best for
Perfect for security teams and system administrators looking for a free, open-source file integrity monitoring tool with extensive customization options.
6. Qualys File Integrity Monitoring
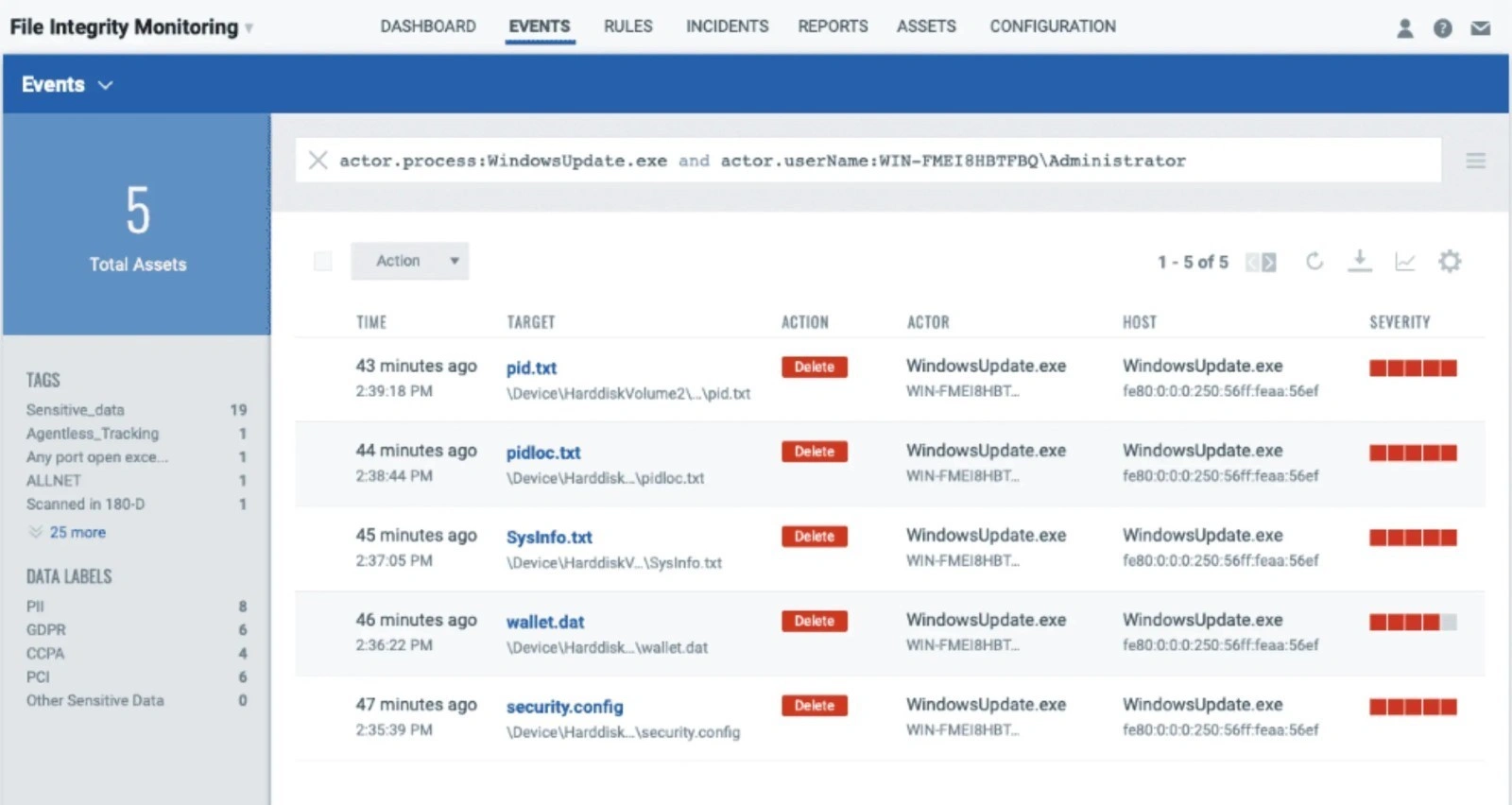
Qualys File Integrity Monitoring (FIM) is a cloud-based security solution designed to detect unauthorized changes in critical files and system configurations. It provides real-time monitoring and detailed logging to help businesses safeguard sensitive data, ensure compliance, and respond swiftly to security threats. With centralized cloud-based management, Qualys FIM enables organizations to maintain a secure IT environment with minimal manual effort.
Key Features
- Continuous Change Detection – Monitors system files, registry keys, and configuration settings in real-time to detect any unauthorized modifications.
- Event Correlation & Analysis – Provides detailed insights into file changes, including who made the change, when, and from where.
- Compliance & Audit Reporting – Helps meet security standards such as PCI-DSS, HIPAA, and GDPR by generating automated compliance reports.
- Cloud-Based Management – Eliminates the need for on-premise infrastructure, offering easy deployment and centralized control.
Best for
Best for cloud-based businesses that require scalable file integrity monitoring with real-time alerts and compliance support.
7. CrowdStrike Falcon
CrowdStrike Falcon is a cybersecurity platform that includes file integrity monitoring as part of its endpoint protection capabilities. It continuously tracks changes in critical files and system configurations to detect suspicious activities. Falcon’s AI-powered threat intelligence enhances security by correlating file modifications with known attack patterns, providing proactive threat detection.
Key Features
- Real-time File Monitoring – Detects unauthorized file and directory changes instantly.
- AI-Driven Threat Intelligence – Uses behavioral analytics to assess whether detected changes are part of a larger attack.
- Scalable Cloud-Native Security – Monitors file integrity across thousands of endpoints without performance issues.
- Automated Alerts & Reports – Generates real-time alerts and detailed reports for security teams.
Best for
Recommended for organizations needing AI-powered file integrity monitoring and endpoint security in a single, cloud-native platform.
8. Splunk Enterprise Security

Splunk Enterprise Security is a powerful SIEM (Security Information and Event Management) solution that includes file integrity monitoring to detect unauthorized changes in system files. It leverages data analytics and real-time alerting to help organizations prevent cyber threats and maintain regulatory compliance.
Key Features
- File Integrity Monitoring (FIM) – Tracks file changes and alerts security teams to potential threats.
- Threat Intelligence Integration – Correlates file modifications with known attack vectors.
- Automated Alerts & Incident Response – Helps security teams quickly investigate and mitigate potential risks.
- Comprehensive Dashboards – Provides visual analytics for monitoring file integrity and security events.
Best for
Ideal for enterprises that require deep security analytics, file integrity monitoring, and correlation with broader cybersecurity events.
Secure your business with real-time file monitoring!
Start using Time Champ’s data protection features today!
Signup for FreeBook Demo9. Cimcor CimTrak
CimTrak by Cimcor is a real-time file integrity monitoring solution designed to protect IT infrastructure from unauthorized modifications. It helps businesses detect, log, and restore unexpected changes, ensuring that critical files and configurations remain secure and compliant.
Key Features
- Live Change Monitoring – Instantly detects modifications to files, directories, and registry settings
- Automated Remediation – Restores altered files to their last known good state
- Detailed Audit Trails – Logs all changes, providing a transparent security record.
- Regulatory Compliance Support – Helps organizations meet compliance requirements for PCI-DSS, HIPAA, and other standards.
Best for
Best for businesses seeking proactive file integrity monitoring with instant rollback capabilities to maintain system stability.
10. Samhain File Integrity
Samhain is an open-source host-based intrusion detection system (HIDS) that includes file integrity monitoring. It is designed for detecting unauthorized changes in system files, monitoring logs, and ensuring security across multiple platforms. Samhain is widely used by security professionals who need a customizable, open-source alternative to commercial FIM solutions.
Key Features
- File Integrity Checking – Monitors critical system files and directories for modifications.
- Log Monitoring – Continuously scans log files to detect security anomalies
- Multi-Platform Support – Works across Linux, UNIX, and Windows environments.
- Centralized Management – Supports monitoring multiple hosts from a single control point.
Best for
Suitable for companies looking for a lightweight, host-based file integrity monitoring tool with stealthy intrusion detection.
How to Choose the Right File Integrity Monitoring Tool

Let’s take a look at some of the key elements you need to check before selecting the file integrity monitoring tools.
1. Ease of Use
A file integrity monitoring (FIM) tool should be easy to set up and manage, even for teams without deep technical expertise. Look for a user-friendly interface, clear dashboards, and simple configuration options that don’t require hours of training. If a tool is too complex, it can slow down response times, making security management more difficult instead of improving it.
2. Scalability
As businesses grow, the number of files, servers, and endpoints that need monitoring increases. A good FIM tool should scale with your needs, whether you’re a small business or a large enterprise. It should handle multiple systems without compromising speed or performance, ensuring that security monitoring remains efficient as your infrastructure expands.
3. Compliance Needs
Many industries, such as healthcare, finance, and e-commerce, have strict compliance requirements like PCI-DSS, HIPAA, and GDPR. A reliable FIM tool should generate detailed audit logs and reports to help meet these legal and regulatory standards. Choosing a solution with built-in compliance features can save time and reduce the risk of non-compliance penalties.
4.Security & Integration
Your FIM tool should offer strong security features, such as encryption, real-time alerts, and automated responses to suspicious activity. Additionally, it should integrate seamlessly with other security tools, such as SIEM (Security Information and Event Management) systems, firewalls, and endpoint protection solutions . This ensures a more comprehensive defense against cyber threats.
Budget
File integrity monitoring tools range in price from open-source solutions to high-end enterprise software. Consider your budget and compare features to determine the best fit for your organization. While cost is important, prioritizing security and compliance features will provide better long-term value and protection against cyber risks.
Prevent unauthorized file changes before they become a threat!
Enhance your security with Time Champ now!
Signup for FreeBook DemoConclusion
A strong file integrity monitoring system helps safeguard your business from security risks and compliance issues. The right tool will ensure visibility, detect unauthorized changes, and integrate well with your existing security setup. Investing in a reliable FIM solution strengthens your overall cybersecurity and keeps your data safe.
Frequently Asked Questions (FAQs)
File Integrity Monitoring (FIM) is a security solution that tracks and detects changes in files, system configurations, and critical data. It helps identify unauthorized modifications that could indicate cyber threats, ensuring data security and compliance.
FIM is essential for businesses to protect sensitive information from cyberattacks, insider threats, and accidental changes. It also helps meet compliance requirements like PCI-DSS, HIPAA, and GDPR, reducing security risks.
FIM alone does not prevent cyberattacks but acts as an early detection system. By identifying unauthorized changes, it allows businesses to take immediate action before a breach escalates.
Yes, some open-source FIM tools, like OSSEC and Samhain, offer basic file monitoring features. However, paid solutions provide more advanced features, better support, and improved security.
Absolutely. Small businesses are often targets for cyberattacks. FIM helps protect valuable data, detect security threats early, and ensure compliance without requiring large IT teams.







