Imagine you just woke up and heard the news about a big company that lost millions just because of a breach .
Scary, right?
For every 39 seconds, one cyberattacks happens. In 2024, the average cost of a data breach reached nearly $5 million. Despite these risks, 45% of employees admit to falling for phishing scams, leading to major data leaks. The reality is clear, cyber threats are growing, and businesses of all sizes are at risk.
That’s where data leak prevention comes in! More than just a DLP tool, it is your weapon to fight against data leaks, insider threats , and costly breaches. In this blog, we’ll cover how it works, why it’s crucial in 2025, and how to protect your business. Let’s dive in!
What is Data Leakage?
Data leakage happens when confidential or sensitive information is unintentionally exposed or disclosed. This can happen when data is stored inappropriately, sent to unauthorized people, or inadequately protected.
While companies may lose their finances directly from data leaks, the biggest damage usually comes from losing trust and reputation. As cyberattacks are becoming pretty common these days, it is important for organizations to improve their security measures to protect against leaks.
Types of Data Leak
Data leaks can happen in many
ways—whether it’s an employee
mistake, a hacker attack, or someone
inside misusing data. Let’s break
down the key types so you know what
to watch out for! /p>

1. Accidental Data Leaks
Accidental data leaks are the most common data leaks that happen in almost every organization. It is often caused by simple mistakes such as sending an email with sensitive information to the wrong person or unintentionally making a database public can lead to major issues. These mistakes are often underseen, so it is important to maintain systems to detect and prevent such errors.
The impact of accidental data leaks can be serious, especially regarding legal and compliance requirements. If a company observes any data breaches, it should immediately report within a certain time. If the organization fails to do so, it can lead to fines and damaged reputation. It is quite costly, and time-consuming as well, which hurts customer trust.
2. Malicious Internal Data Leaks
Malicious internal data leaks occur through trusted employees or contractors within the organization, who intentionally expose sensitive information. This could be due to a variety of reasons such as for personal gain, sabotage, etc. The biggest challenge with these data leaks is that these people have authorized access to company systems, which makes it difficult to detect any malicious activities until major damage is done.
What makes this data leak more dangerous is that they know every little detail about the organization’s security weaknesses and can exploit them. These leaks can harm the company legally and damage its reputation. To avoid this, companies should control who has access to data, watch employee actions, and teach staff about the legal and ethical problems of data theft.
3. Cloud Data Leaks
With the increasing dependency on cloud services, cloud data leaks have become a major concern for businesses and individuals alike. These types of leaks usually occur due to misconfigured settings, and weak access controls in the cloud platform.
For example, if a cloud storage service such as AWS S3 is not properly secured, it can accidentally expose confidential data to anyone on the internet.
As many companies are migrating to cloud services, the risk of cloud leaks is increasing as well. Cloud services offer scalability and cost-efficiency, but they also require careful management and attention to security settings. A small mistake in settings can cause data leaks which affect millions of customers.
4. Malicious Data Leaks
Malicious data leaks happen when external attackers use hacking, and phishing to steal sensitive data. These methods are getting more advanced as cybercriminals improve their methods to bypass security. Once hackers crack the system, there isn’t a limit to their data stealing, which makes the problem even worse.
The consequences of malicious data leaks can be devastating. Along with the financial impact, organizations may go through long downtime, disruptions in their daily work, and damage their reputation.
5. Third-Party Data Leaks
Third-party data leaks occur when a business partner, vendor, or contractor experiences a data breach that compromises sensitive information shared with them. Third-party vendors usually don’t maintain the same level of data security that your organization follows.
The problem with third-party data leaks is that you cannot fully control the security of your partners. Despite the checking and contracts, it is still almost impossible to ensure that they adhere to the same level of data protection. That is why businesses have to select their partners more carefully, monitor their security, and ensure that third-party contractors adhere to the rules of data protection to minimize the chance of a breach.
Benefits of Data Leak Prevention

1. Improves Data Security
One of the main benefits of using data leak prevention (DLP) is better security for important information. DLP systems help monitor, detect, and prevent any unauthorized access to confidential information, such as customer data, financial records, and intellectual property. By keeping information secure, businesses can reduce the risk of internal or external threats that could expose sensitive data. DLP ensures that only the right people can see certain information, making leaks much less likely, whether by accident or on purpose.
2. Protects Brand Reputation
A data leak can have a devastating impact on a company’s reputation. Customers trust companies to protect their personal and financial information, and a breach of that trust can lead to a loss of customers, negative press, and long-term damage to the brand. Data leak prevention not only protects reputation but also shows customers and partners that they prioritize data security. It is crucial for a business to have a good reputation for protecting data since some industries place a high value on privacy.
3. Compliance with Regulations and Legal Requirements
Data leak prevention is very important for companies that have to follow rules like GDPR, HIPAA, or CCPA. These rules require businesses to protect personal and sensitive information. If they don’t, they could face large fines, legal trouble, and damage to their reputation. DLP systems help companies follow these rules by keeping sensitive data safe and providing reports that show they are meeting the requirements.
4. Mitigation of Financial Loss
Who doesn’t want to save money? Data leaks are costly, not only in terms of legal fines but also due to the direct financial loss that can occur from theft of intellectual property. With data leak prevention, companies can eventually avoid spending money on financial loss that comes with a burden. Additionally, DLP tools can help prevent the loss of valuable trade secrets or sensitive financial information, protecting the company’s bottom line and reducing the risk of costly recovery efforts.
5. Increases Employee Accountability
Data leak prevention improves internal security by monitoring, detecting, and preventing unauthorized access or file transfers. By using DLP solutions, organizations can track file-sharing activities, and copy files to external devices, and businesses can identify and address potential risks before they become major issues. This improves employee accountability and creates a culture of security that teaches employees about the importance of data protection and the severe consequences of data mishandling.
Limitations of Data Leak Prevention
While data leak prevention is a powerful security tool, it’s not foolproof. There are some limitations which should be looked forward to.

1. False Positives and Negatives
Data leak prevention systems aren’t perfect, and can sometimes create false positives and negatives. False positives happen when normal file transfer is flagged as a data leak. On the other hand, false negatives occur when an actual data breach goes unnoticed, which can be more dangerous. Both scenarios create a lot of mess. False positives lead to unnecessary alerts, and disruptions whereas false negatives could lead to a big disaster in terms of everything.
2. Complex Configuration and Maintenance
We know how effective DLP works but have you ever thought about how the setup process goes?
Setting up DLP solutions can be tricky and requires continuous adjustments to work well. If the system is not configured correctly, it could either be too lenient, letting data leaks go unnoticed, or too strict, disrupting normal business activities. The key is to find the right balance to make sure the system protects sensitive data without interfering with daily tasks.
3. Bypass Methods
Skilled users, especially those with bad intentions inside the company, can sometimes find ways to get around DLP systems. For example, they might use encryption to hide data, store it on personal devices, or upload it to cloud services that the company doesn’t control. These tricks help them avoid security measures, making it harder for the DLP system to catch the data leak.
This is a big challenge for DLP systems, as they can only detect what they are programmed to find. If sensitive data is hidden or moved in ways the system can't track, it may go unnoticed. To prevent this, businesses need to regularly update and improve their DLP systems to keep up with new ways people might try to bypass security.
4. Impact on User Productivity
Over-strict DLP policies can slow down by blocking things such as file sharing, which can lead to frustration and delays. Regular alerts, notifications, and restrictions just get in the way and make it harder for employees to do their jobs.
The goal is to balance data security with letting employees work without being interrupted all the time. Data security is important, but the DLP system should not make everyday tasks harder.
Best Practices for Data Leak Prevention
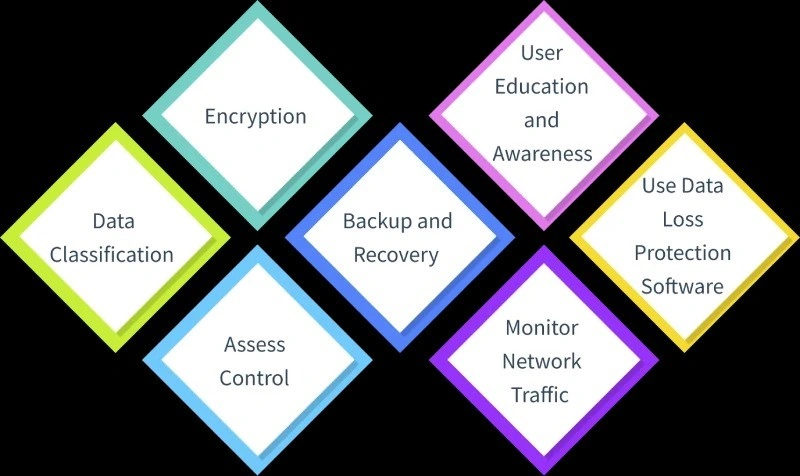
1. Data Classification
Data classification helps organizations categorize information based on sensitivity. This makes sure that appropriate security measures are applied to protect confidential information. By defining access controls and encryption based on classification, companies can mitigate risks of exposure and make sure compliance with regulations.
Clear sorting of data makes it easier to check and control, reducing the chance of someone getting in without permission or accidentally leaking it. It's important to keep things like personal details, money info, and business secrets safe.
2. Encryption
Encryption converts sensitive data at rest and in transit into unreadable code so that it can only be accessed by authorized users. This form of encryption is important for securing data transmitted via networks or stored on devices.
It protects data even if devices are lost or stolen, and strong key management practices support encryption integrity. Updating encryption regularly is key to protecting data against threats.
3. Assess Control
Access control must be regularly assessed to ensure that only authorized individuals can access sensitive data. Regular reviews and updates of access rights can help avoid unauthorized access. Role-based access control (RBAC) is a critical component that helps to allow access to data depending on the user’s role, restricting permissions only to what they need to do their jobs.
Staff transitioning into new roles may require different access privileges, so ensuring permissions are amended is critical. Regular checks are necessary, otherwise users may end up having access to more data than they actually need, leading to privilege escalation or unauthorized information access.
4. Backup and Recovery
Regular backups of important data can help protect against data loss, system failure, and cyberattacks. Keeping these backups stored in a secure location, preferably offsite or in the cloud, will provide the ability to quickly recover in the event of emergencies. This process minimizes data loss and downtime. Regular testing of backup processes helps ensure their effectiveness and identify any weaknesses before a crisis happens.
Strong security measures such as strong encryption, should be implemented to protect backup data both in storage and during recovery. Encryption prevents unauthorized access and ensures compliance with data protection regulations.
5. User Education and Awareness
Many data leaks happen due to a lack of proper knowledge of security risks. To avoid this, it is important to give regular training to employees as it helps them to recognize security threats such as phishing, social engineering, unsafe data handling, etc. By implementing a culture of security awareness, organizations reduce the risk of human errors which leads to data breaches.
Clear guidelines on data access, storage, and handling of sensitive data help employees to get a better idea. Regular reminders reinforce these policies, keeping employees vigilant and compliant.
6. Monitor Network Traffic
Data leak prevention systems constantly monitor network traffic to keep the information safe. They track the data seamlessly as it moves through the company network and can spot possible risks right away. If something appears to be unsafe, security teams can capture it, analyze the issue, and prevent data leakage within minutes.
These tools can also automatically block malicious actions when danger is detected. Data movement tracking allows teams to get a better picture of security risks, generate reports, and ultimately offer better protection. This helps to keep information secure and makes sure everyone complies with security regulations.
7. Use Data Loss Protection Software
The major step to take is to adopt data loss protection software. Data loss protection software detects and blocks the sharing of sensitive data to unauthorized destinations, preventing data breaches. It monitors file movements across networks and devices, setting guidelines to protect private data.
Last but not least, using strong data loss protection is a must—and that’s where Time Champ makes a difference. It goes beyond basic security by providing real-time tracking, instant threat alerts, and automatic controls to stop data breaches before they happen. It watches file movements across networks and devices, keeping sensitive information safe and making sure data-sharing rules are followed.
With powerful encryption, smart access controls, and easy integration, Time Champ gives businesses complete security. It blocks unauthorized file transfers, detects insider threats, and helps meet security rules. By choosing Time Champ, businesses can stay ahead of risks, protect important data, and create a safer digital workspace.
Protect your sensitive data with Time Champ's Data Loss Protection.
Detect, prevent, and respond to potential data leaks in real-time—keeping your business secure and compliant!
Signup for FreeBook DemoFinal Thoughts
In conclusion, data leak prevention helps to protect sensitive information, ensuring compliance and trust. While it has some challenges and false alerts, its benefits such as better protection, cost savings, and a strong reputation make it essential. A smart approach secures data without slowing down work.
Frequently Asked Questions
Not really, if settings are not configured properly, DLP can create unnecessary restrictions. However, a properly configured DLP system secures data without affecting productivity.
No, DLP benefits businesses of all sizes. Every business handles sensitive data and must protect it from leaks and cyber threats.
Costs usually vary, but there are many affordable DLP solutions for small businesses. Investing in DLP saves money and reduces spending money on preventing data breaches.
Yes, DLP can block data transfers to unauthorized mobile devices and protect company data on personal devices. It ensures sensitive information stays secure, even on employee-owned phones or tablets.







